2.4 Privacy and emotional safety with ICT
Have you ever had junk mail arrive specifically addressed to you? Did you think, how did they get my address? Likewise, do you have junk email sent to you? You didn’t request it, yet it’s been sent to your address. How did they get your email address? Why do they think you might be interested in what they are selling or saying?
You would probably be surprised at how many organisations have details about you in their database. These organisations can be government, semi-government or private/commercial.
For legitimate reasons, your details will be stored with government organisations. At birth, your details were registered and the process continues from there on. Visits to the doctor go on file, with address, medical records and so on. When you started school, more details went into the system. Your address details and family status may be updated. These types of records are confidential and are not passed on to third parties.
There are other scenarios where you can be unwittingly handing out personal details to a range of people. A simple example is purchasing an item through lay-by or online (ecommerce). You give your name and address to the shop assistant who enters it into the store database. In this way the store can start to build a customer database, which they can use for their own advertising purposes or sell to other commercial enterprises who use the details for their advertising – hence the junk mail addressed to you.
The Flybuys cards store details about you. They can also store details about the items you purchased. The retailer can develop a profile on their customer and use this to their advantage.
Competitions are a classic data-building exercise. This could be seen to be relatively harmless because, in the end, the retailer is trying to give us what we want. However, do you know what the promoters do with your details when the competition is over? These simple examples remind us that we all leave a digital footprint online.
There are other areas where details stored about you can be a distinct disadvantage. A simple example of this is credit ratings. When your home is connected to electricity you are expected to pay the resulting bills promptly. This applies to all bills, credit cards, mobile phone, store cards and so on. If you repeatedly do not pay on time, you risk being listed as a credit risk. This may not affect you immediately, as you still have your electricity, credit card and mobile phone.
However, when you go to the bank for a loan to buy a car or home, or a finance company to buy a computer or some other large piece of equipment, you may be denied. These companies always check credit ratings before lending money. If you are listed as a credit risk, you will be unlikely to get a loan. Your details are stored, along with your credit rating for the past five years. The company may be wise not to lend you money.
On the other hand, it may not have been your doing that you now have a bad credit rating. You may never have received the bill that you are now listed as not having paid. They may be looking at the details for the wrong person. The data entry operator may have entered the details incorrectly. The person doing the checking on the payments may not have scrolled up high enough to see that payment had actually been made. The information in a computer is only as accurate and safe as the person entering it or able to modify it.
A different example is if you win Tattslotto – but you want to keep it quiet because you don’t want others hounding you. You deposit the money into your bank account – you go to another town to do it because you don’t want the locals to know. How many people do you think have access to your bank account details?
Another example is when you visit your local doctor, who enters your latest medical condition onto the file on screen then puts your paper file away and sends you on your way (but doesn’t close the screen on the computer). Their next patient is a friend of your mother’s with very good eyesight. How safe are your medical records?
- Can you recall the last three times where you gave personal details, either in written or electronic form? What was the purpose and who was it to? Do you know what each organisation will do with your details?
- Think about the organisations who record details about you and discuss in a group or as a class the rules or protocols that these organisations should adhere to in order to protect your privacy.
Rapid advancements in technology and the ability to gather information about an individual are making it increasingly difficult to control the information stored on an individual, who has access to it and for what it is used. The Privacy Amendment (Private Sector) Act 2000 is an attempt to increase protection of individuals’ right to privacy and the use of personal information about them.
More information can be obtained at the Office of the Australian Information Commissioner website.
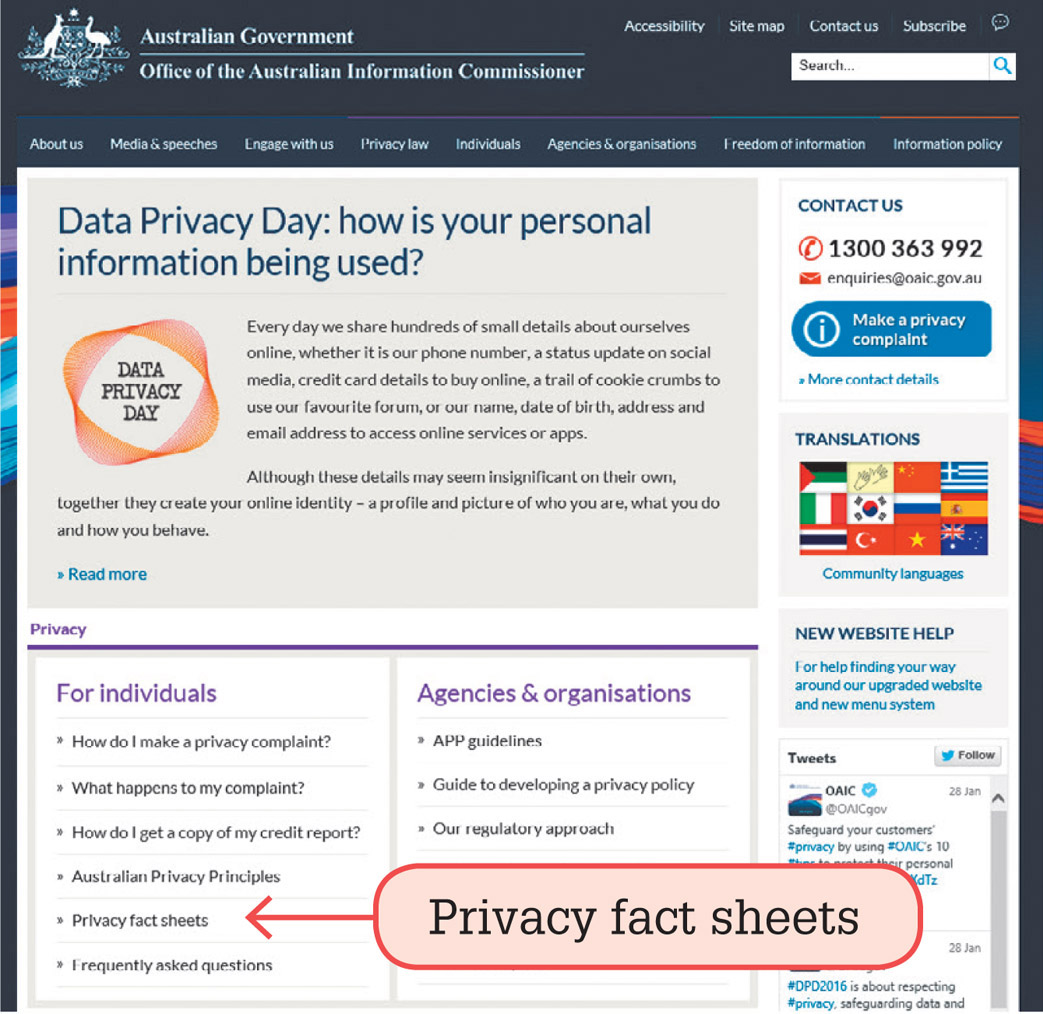
- Go to the Office of the Australian Information Commissioner website.
- Under ‘For individuals’, click on ‘Privacy fact sheets’.
- Scroll through until you find ‘Privacy fact sheet 8: Ten tips to protect your privacy’.
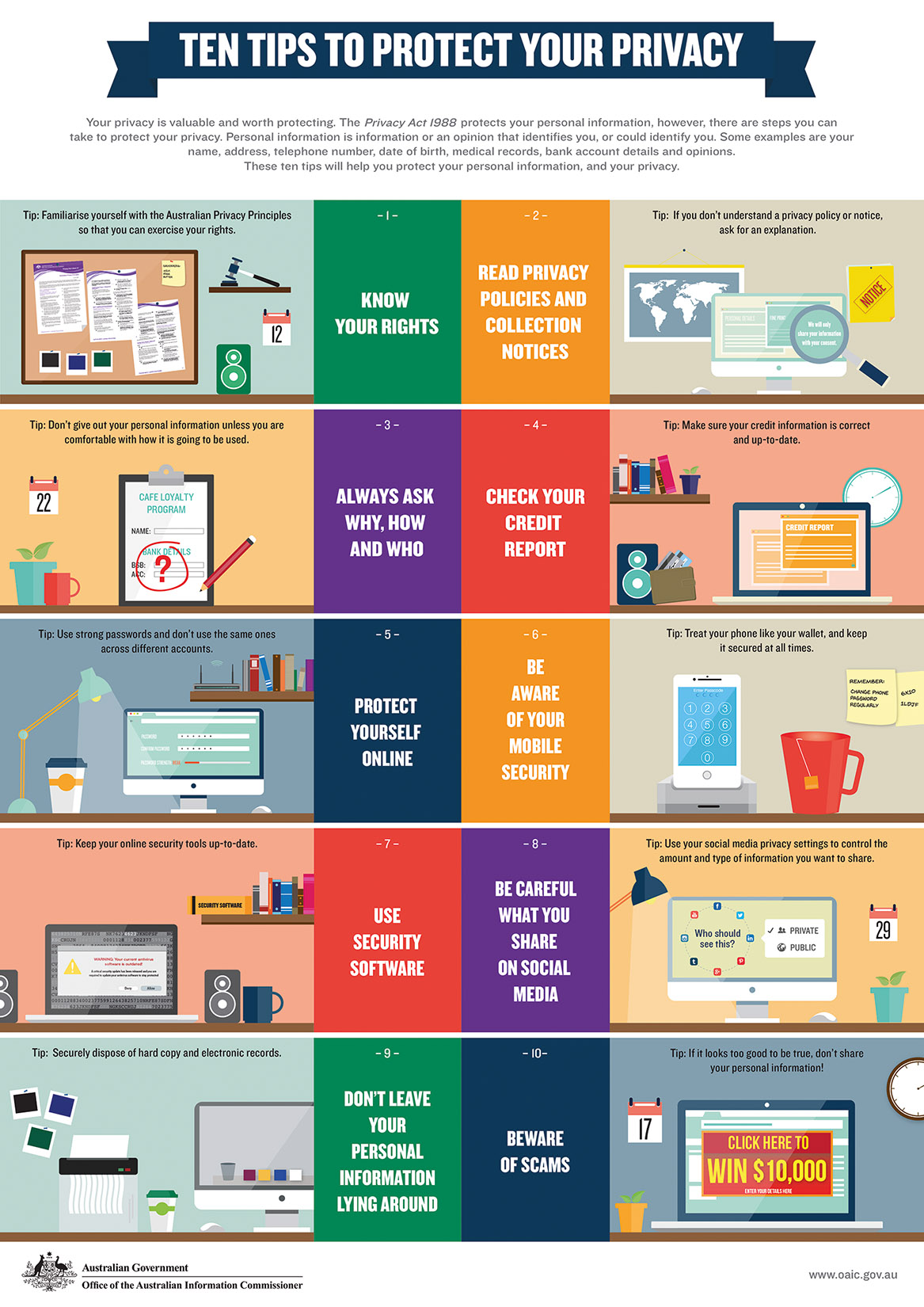
- Click on the link to the sheet. This fact sheet is a good summary of steps you should take to protect your personal information.
- Look for the ‘Privacy fact sheet 7: Ten steps to protect other people’s personal information’.
Social and ethical practice in IT exercise 8
Create a presentation on privacy
- Design a presentation that could be used to educate others on protecting their privacy based on ‘Privacy fact sheet 8’ and others privacy based on ‘Privacy fact sheet 7’.
- Enter text and images to illustrate each step.
- Save the file as ‘Ten steps to protect your and others’ personal information’ in the folder.
- Share it with your friends and classmates to get feedback.
- Make any modifications you think necessary or an improvement.